How Phones and Apps Revolutionized Business Everywhere
In the contemporary business landscape, mobile phones and mobile applications have seamlessly integrated themselves as indispensable facets of a company’s digital presence. Enterprises now heavily lean upon mobile applications as a vital means to establish global connections with their user base.
The realm of mobile application security encompasses the holistic safeguarding of mobile applications, spanning the diverse domains of Android and iOS, which represent the foremost pillars of mobile technology. This domain encompasses applications tailored to run on both mobile phones and tablets alike. It entails a comprehensive evaluation of these applications for potential security vulnerabilities within the contexts of their designated platforms, the underlying development frameworks employed, and the intended audience, be it internal employees or end users.
The transformative debut of the inaugural iPhone in 2007 was a pivotal moment in the evolution of mobile applications. It ushered in an era characterized by groundbreaking hardware innovations, a user-centric interface, and the establishment of a centralized App Store. This catalyzed the emergence of a vibrant and thriving ecosystem for the development of mobile applications.
Unlocking the Pandora’s Box: Navigating Security Challenges in Mobile Phones and Apps
With the rise of smartphones and app usage, addressing application security is an unavoidable necessity to guarantee business and revenue security. For businesses especially, the risks need to be addressed and countered to prevent several potentially disastrous consequences. Mobile applications commonly grapple with a set of recurring challenges, which encompass the following:
- Inadvertent Exposure of Sensitive Data: This pertains to the inadvertent storage or disclosure of confidential information in a manner that permits access by other applications residing on the user’s mobile device.
- Lax Authentication and Authorization Measures: The implementation of inadequate authentication and authorization protocols poses vulnerabilities that can be exploited by malicious applications or malevolent users, potentially leading to unauthorized access.
- Susceptible Data Encryption Techniques: The use of encryption methods with known vulnerabilities or those susceptible to facile decryption introduces security risks, compromising the confidentiality of data.
- Unencrypted Transmission of Sensitive Data: The transmission of sensitive data sans encryption over the Internet represents a significant peril, as it exposes the information to interception by unauthorized parties.
These issues harbor the potential for exploitation through various avenues. Malicious applications residing on a user’s device or nefarious actors with access to the same WiFi network as the end user are examples of entities that may seek to exploit these vulnerabilities.
Guarding Your Mobile Fort: A Closer Look at OWASP’s Top Ten Mobile App Security Threats
Similar to OWASP’s Top Ten for Web Applications, OWASP publishes a list of categories of top vulnerabilities affecting mobile apps. The OWASP Mobile Top 10 list includes security vulnerabilities in mobile applications and provides best practices to help remediate and minimize these security concerns. Organizations building mobile applications should minimally refer to the Top Ten list to build appropriate defenses that can handle static attacks based on source code and dynamic attacks that exploit application functionality.
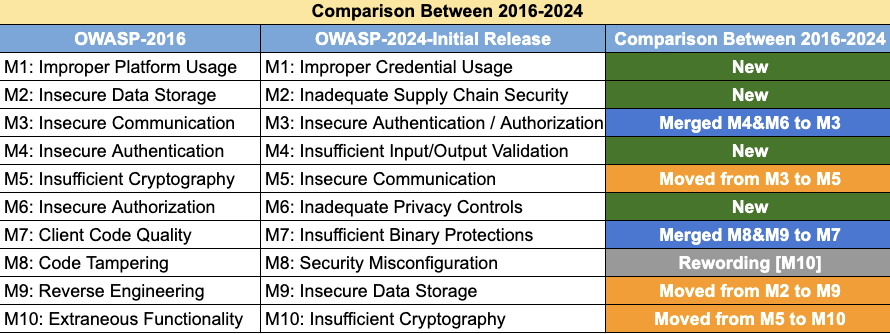
- M1: Improper Credential Usage
- M2: Inadequate Supply Chain Security
- M3: Insecure Authentication/Authorization
- M4: Insufficient Input/Output Validation
- M5: Insecure Communication
- M6: Inadequate Privacy Controls
- M7: Insufficient Binary Protections
- M8: Security Misconfiguration
- M9: Insecure Data Storage
- M10: Insufficient Cryptography
OWASP Mobile Top Ten list is its 3rd iteration. The first list of made public in 2014.
Here is the list of changes to Mobile Top between 2016 and 2023
Crafting a Shielded Haven: Essential Security Best Practices for Mobile App Development
There are several checks for backdoors or extraneous functionality that an app developer should make before releasing an application or publishing an update to it. These include:
- Having a trusted third party manually revise the code
- Examining and documenting all API endpoints
- Revising information and descriptions contained in log statements
- Removing all test code from final releases
- Checking configuration settings to ensure no easy access to extra functionality is inadvertently granted
Coding with Confidence: Supercharging Your CI/CD Pipeline with Security
Incorporating security testing tools into your Continuous Integration/Continuous Deployment (CI/CD) pipeline is essential for identifying and addressing security vulnerabilities early in the software development process. This will allow organizations to proactively identify and remediate security vulnerabilities, reducing the risk of security breaches and improving the overall security posture of your applications.
These are some of the recommended security scanning one should do (but not limited and inclusive):
- SAST
- SCA
- API Security
- Secrets Scanning
- Pen Testing